🔍 Resources
URI-based access to Arch ecosystem data - read documentation, package info, and system state.Resources Reference
23+ URI schemes for accessing Arch Wiki, AUR packages, official repos, system data, logs, news, configuration, and mirrors

- Access Arch Wiki pages in Markdown format
- Fetch PKGBUILD files with safety annotations
- Query AUR package metadata
- Look up official repository packages
- List installed packages (Arch only)
🛠️ Tools
Executable functions for search, security analysis, and package installation.Tools Reference
41 tools organized into 9 categories: discovery, lifecycle, maintenance, organization, security, monitoring, history, mirrors, and configuration

- Search Arch Wiki and AUR packages
- Analyze PKGBUILD files for security risks
- Evaluate package trustworthiness
- Check for system updates safely
- Install packages with automated security checks
📋 Prompts
Guided multi-step workflows that combine resources and tools for complex tasks.Prompts Reference
8 intelligent workflows for troubleshooting, security audits, dependency analysis, system updates, cleanup, and health checks
- Diagnose system issues with Wiki-guided solutions
- Audit AUR packages before installation
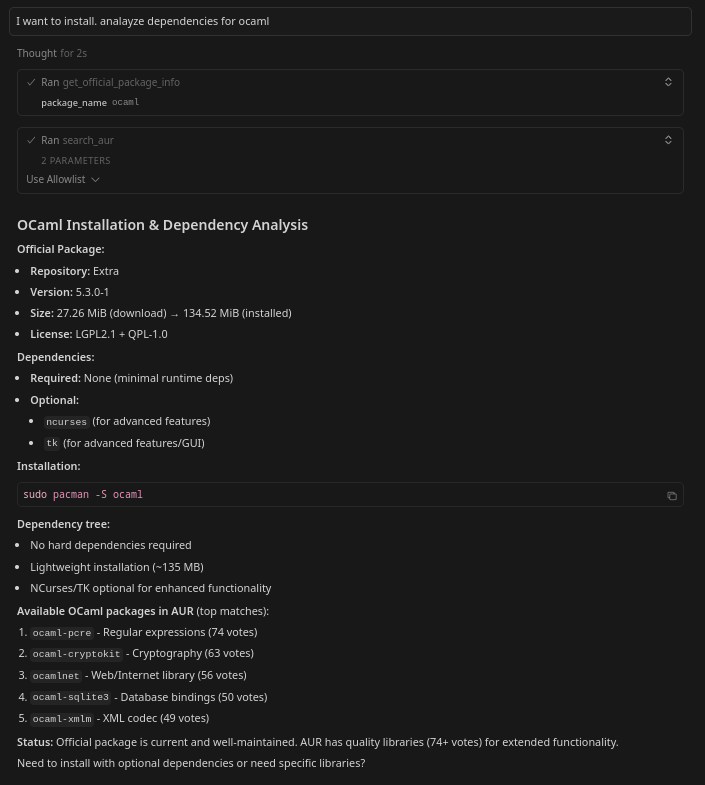
- Plan installations by analyzing dependencies
Feature Comparison
Quick reference to understand what each capability type offers:| Capability | Count | Access Method | Use When | Example |
|---|---|---|---|---|
| Resources | 23+ | URI schemes | Need raw data or documentation | archwiki://Systemd |
| Tools | 41 | Function calls | Need to perform operations | search_aur query="vim" |
| Prompts | 8 | Workflow triggers | Need guided multi-step process | audit_aur_package |
Best Practice: Combine all three types for powerful workflows! Resources provide data, Tools perform operations, and Prompts orchestrate complex tasks.
How They Work Together
See how Resources, Tools, and Prompts combine to solve real problems.Interactive Workflow Example
User asks a security question
User Query:
The AI assistant automatically determines the best workflow for this request.
Resource: Fetch PKGBUILD
Resource Access:The system uses the PKGBUILD resource to fetch the raw build script for inspection.
Tool: Analyze PKGBUILD Safety
Tool Execution:Scans for security threats:
- ✅ Dangerous commands (
rm -rf /,dd, etc.) - ✅ Suspicious downloads (
curl|sh,wget|bash) - ✅ Obfuscated code (base64, eval)
- ✅ Privilege escalation attempts
Resource: Get Package Metadata
Resource Access:Provides community trust indicators:
- Popularity votes (2,500+)
- Maintainer information
- Last update date
- Package age and history
Tool: Evaluate Trust Score
Tool Execution:Evaluates:
- Is the maintainer trustworthy?
- How popular is this package?
- Is it actively maintained?
- Any red flags in metadata?
Trust score: 85/100 - High community trust
Automation: The entire workflow above can be triggered with a single prompt:
audit_aur_package package="neofetch"Workflow Visualization
Capability Statistics
23 Resources
URI-based data access for Wiki pages, PKGBUILDs, package info, and system data
41 Tools
Executable functions across 9 categories for all Arch Linux operations
8 Prompts
Guided workflows for troubleshooting, auditing, system updates, cleanup, and health checks
Tools by Category
| Category | Tool Count | Permission | Common Uses |
|---|---|---|---|
| 🔍 Discovery & Information | 6 | Read | Search Wiki/AUR, get news |
| 📦 Package Lifecycle | 4 | Write | Install, update, remove packages |
| 🔧 Package Maintenance | 7 | Mixed | Verify, mark, clean orphans |
| 📁 File Organization | 5 | Read | Find owners, list files, search |
| 🔒 Security Analysis | 2 | Read | PKGBUILD/metadata scanning |
| 📊 System Monitoring | 5 | Read | Disk space, services, logs |
| 📜 Transaction History | 4 | Read | Audit package operations |
| 🌐 Mirror Management | 4 | Read | Test speed, suggest mirrors |
| ⚙️ Configuration | 4 | Read | Parse pacman/makepkg configs |
Platform Support:
- 17 tools work on any platform (use remote APIs)
- 24 tools require Arch Linux (use local system)
- All resources work on any platform